Personal VPN services have been advertising aggressively. Listen to just about any podcast or radio show for a while, and you’ll hear a message like: “If you leave your internet connection unencrypted, your passwords and credit card numbers could be vulnerable to bad people or Batman…” (I kid you not).

☝️ That’s good ad copy, but bad security advice. Save your $7/month for something more fun. Unless you have a few pretty specific goals, you don’t need a VPN for personal protection. Here’s why.
Batman Can Break Through Any and All Encryption
Let’s get the most obvious thing out of the way. There’s no escape from the Dark Knight. If you plan to hide your traffic from a vigilante billionaire with impossibly savvy henchmen, you plan in vain. He’ll just hack every cell phone in the city and spy on you directly.
You’re Already Using Strong Encryption
Whenever you read a website, check your email, or join a video call, your phone sends requests to the internet. In the old days, those looked a little something like this:
S: 220 smtp.example.com ESMTP Postfix C: HELO relay.example.com S: 250 smtp.example.com, I am glad to meet you C: MAIL FROM:<[email protected]> S: 250 Ok C: RCPT TO:<[email protected]> S: 250 Ok C: RCPT TO:<[email protected]> S: 250 Ok C: DATA S: 354 End data with . C: From: "Bob Example" <[email protected]> C: To: Alice Example <[email protected]> C: Cc: [email protected] C: Date: Tue, 15 Jan 2008 16:02:43 -0500 C: Subject: Test message C: C: Hello Alice. C: This is a test message with 5 header fields and 4 lines in the message body. C: Your friend, C: Bob C: . S: 250 Ok: queued as 12345 C: QUIT S: 221 Bye {The server closes the connection}
That’s a bit verbose, but if I squint, I can kinda make out that this request is an email from someone named Bob to someone named Alice. I can see the subject line and the text of the message because the request isn’t using any kind of encryption.
This kind of request used to travel from the desktop mail program of someone like Bob to their router, then to their ISP, to the internet backbone, to Alice’s ISP, to Alice’s router, and then finally end up on Alice’s desktop email program. During the trip, the message could be read by anyone along the way—a bored employee at the local ISP, a government with a wiretap, a vigilante billionaire. Anybody.
That should terrify you. In fact, forget what I said. You definitely need a VPN. Anyone can read your emails. You need all the protection you can get!
Whoa. Sorry. Got carried away there. Things aren’t nearly that bad anymore. We don’t have to worry so much because most requests don’t look like that today. Virtually every email provider, every website that houses anything remotely sensitive, and every internet communication channel uses an encrypted line. Today, an email request looks a lot more like this:
ApplicationData message
0000 17 03 01 00 30 5d 15 3d a2 40 ef d2 01 25 ca 54 ....0].=.@...%.T
0010 26 5f 5d b0 d2 2f 2f 6d 2d ec 56 85 b0 4c a9 bf &_]..//m-.V..L..
0020 eb 97 be 31 ad cd de 3a b4 71 1e c8 53 96 0b 2d ...1...:.q..S..-
0030 c3 91 3d a2 15 ..=..
17 ApplicationData protocol type
03 01 SSL version (TLS 1.0)
00 30 Message length (48 bytes)
5d .. 15 Encrypted application data
As far as anyone delivering the message is concerned, it’s just noise. Only someone with the right key can decrypt it into an actual email. For our purposes here, it doesn’t matter how the encryption happens, but if you’re interested in learning more about it, Mike gave a really good talk at RailsConf a couple of years ago that you should check out.
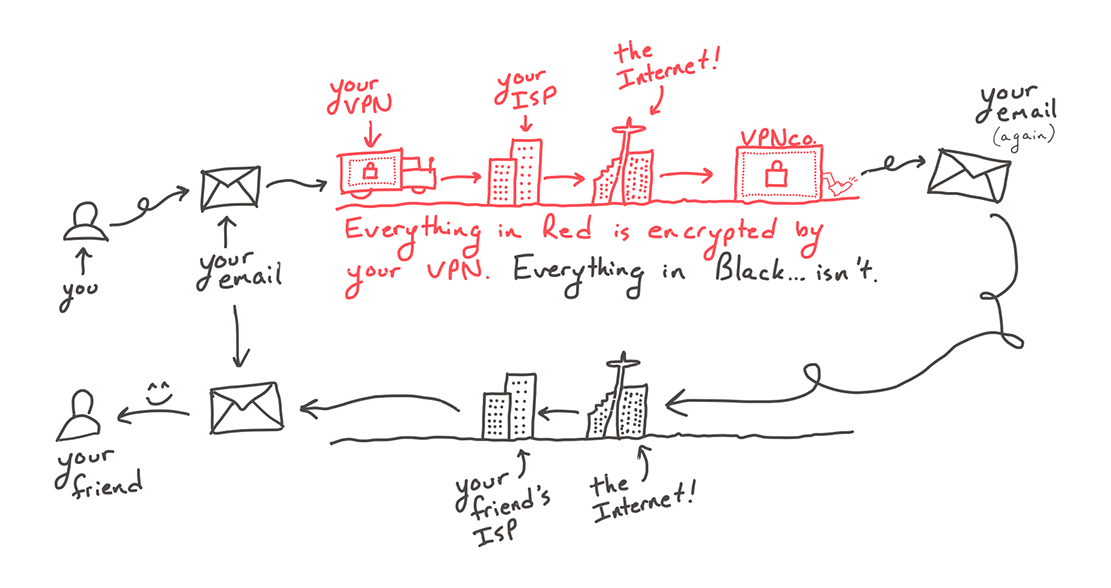
A VPN Only Gets You Halfway There
An armored car only protects you as long as you’re inside it. When you send requests through a VPN, your phone wraps them in a thick layer of encryption that only you and the VPN company know how to unlock (the armored car). It then dutifully drives the requests to the VPN company’s computer. Upon arrival, your requests are unceremoniously shoved out the back door of the car and told to hitchhike the rest of the way to your friend’s ISP. Your VPN couldn’t care less who takes them the rest of the way.
For this reason, VPNs aren’t all that good at preventing hackers from getting the credit card information you send to Amazon. To protect yourself online, you need a secure code that only you and Amazon know. That’s what TLS is for (seriously, watch Mike’s talk, it’s great), and that’s the security that nearly every service you interact with already uses today. Automatically. You don’t even have to pay $7/month for it.
VPNs Are Awesome
VPNs are really good at doing a few very specific jobs. If you want to reduce the attack surface of your on-prem software installations, bounce your requests around the globe to test latency in other countries, or hide the names of the sites that you visit from your ISP, then by all means, use a VPN.
But don’t shell out your hard-earned cash just so you can use public WiFi “safely.” Unless you’re using very, very old sites and services, your requests are already safe from the prying eyes of your fellow café patrons. Not from Batman though. No encryption is that good. 🦇🔓
Well, Actually… 🧙♂️
- But Joe, emails aren’t encrypted in transit.
That’s mostly true. Most email providers will connect to your email app over a secure line if the app supports it, and most email apps try to do so when connecting to the major email providers, but what the providers do with the message after you securely hand it to them is anybody’s guess. There is some evidence that some of the major providers offer secure connections when sending messages to receiving mail servers, but that behavior is entirely behind the scenes, and optional. It’s best not to send sensitive information over email unless you first encrypt the message with end-to-end with tools like PGP or GPG. In any case, VPNs don’t improve the security of your emails. - But Joe, DNS requests aren’t protected by TLS, so people on public WiFi can see the addresses of the sites that I’m visiting.
Yeah, they can. There’s an effort to change that. But until that takes off, people on public WiFi will be able to see the domain names of the sites that you visit. If this bothers you, use a VPN, I guess. 🤷♂️ Or, better yet, use a DNS provider that supports DNSSEC. - But Joe, not every site uses TLS.
It’s true. There are still a lot of sites on the internet that don’t use encryption. It’s totally fine to read them, but you should never give them sensitive information. Using TLS is a basic requirement for any modern site that does anything with your data. - But Joe, TLS relies on a complex network of trusted authorities, including a post office in Hong Kong for some reason.
It does. If someone on a public WiFi network intercepts your requests, and they have the private keys from a public certificate authority, they might be able to read your email. Sometimes those keys are divulged accidentally. But it’s pretty rare, and OS vendors take it very seriously. Most browsers and apps take precautions against this kind of attack anyway with techniques like certificate pinning. - But Joe, I live in a country that prohibits my favorite internet pastime, and I need a VPN to break through to the outside world.
You should definitely use a VPN. They’re great at this. - But Joe, that example of an encrypted email message isn’t actually an encrypted email message.
🤷♂️ You got me. I googled around for an example of a realistic SMTP over SSL payload and this was the closest thing I could find after a 10-minute search. I think it gets the notion across. - But Joe, my favorite podcast host says that I definitely need a VPN.
Yeah…they also say you need pillows made of buckwheat, subscription socks, and silver-lined underwear…so…maybe take their advice with a dash of premium kosher salt that you bought online, using the code #WiFiIsFine at checkout to get 10% off your first order.