Article summary
You know and use personas for a majority of your projects, but I’m here to tell you that you may have missed a category of user. A very important one. A not-so-friendly one.
Users Who Mean Harm
 Let’s pretend you’ve created a beautifully functioning and user-friendly app. It’s living and breathing in the world when, BAM! An unfriendly, nay malicious, user begins threatening your ecosystem by attempting to scam your users or utilize your service for wrongdoing.
Let’s pretend you’ve created a beautifully functioning and user-friendly app. It’s living and breathing in the world when, BAM! An unfriendly, nay malicious, user begins threatening your ecosystem by attempting to scam your users or utilize your service for wrongdoing.
But who are these dark evil-doers? Here are a few examples:
- Fraudsters – Those looking to scam users from money or identity details
- Terrorists – Those looking to use your service to purchase unsavory goods, transfer sensitive information, or obtain illegal materials
- Predators (Sexual or Abusive) – Those looking to use personal information to stalk, assault, or hurt others
Think I’m being dramatic or extreme with these examples? These are real users, and I’ve worked with clients who have dealt with some from each category. And though they might not be as numerous as your “light” users, they can inflict the most damage. It’s a sad, but true, reality.
If you thought the tech industry grew quickly, take a peek at the fraud “industry.” Companies are struggling to keep up with ever-changing techniques that fraudsters use to score your information. And it’s not just information that’s being lost. It’s millions of dollars, personal property, and at times, human dignity.
One of the biggest pain points is that every time a new roadblock is built, fraudsters find another workaround. Oh, and Merry Christmas! Fraud increases by 20% every holiday season. Santa is not pleased.
The good news is that you can prevent fraud from happening even before launch with a process you already know. You’re going to build user personas and flow maps like you always do, but this time, you’re going to consider including villainous users.
This step isn’t always necessary, but in over half of the projects I’ve worked on this year, it was more than necessary. It was vital to the success of the application.
Thinking Like the Enemy
Let’s break this down a bit, and I’ll show you some quick examples of how you can include fraudulent users in your process.
The story
 We’ll start by setting up some fake context. Imagine that we’re building an application for an international shipping service. Mixed in with the regular users and their endless shipments of jeans and baby formula are villainous users attempting to ship 50-gallon barrels of pool sanitizer to build homemade bombs. Fortunately, the company has been around for many years, so they have ample data on their villainous users.
We’ll start by setting up some fake context. Imagine that we’re building an application for an international shipping service. Mixed in with the regular users and their endless shipments of jeans and baby formula are villainous users attempting to ship 50-gallon barrels of pool sanitizer to build homemade bombs. Fortunately, the company has been around for many years, so they have ample data on their villainous users.
The process
Now, let’s work this into a process.
1. Identify your users
If you need a refresher on user personas, check this out. When defining your personas, determine who all your major user groups are and whether or not to include villainous users based on their potential to threaten your app/service.
2. Research your bad actors
 This is where things become a little tricky. This practice isn’t as straightforward as creating a “light” persona because you won’t be able to ring up a terrorist for a user interview. You need data. Data can reveal fragments of your villainous users’ motivations, desires, and goals. It’s your job to glue the fragments into a persona.
This is where things become a little tricky. This practice isn’t as straightforward as creating a “light” persona because you won’t be able to ring up a terrorist for a user interview. You need data. Data can reveal fragments of your villainous users’ motivations, desires, and goals. It’s your job to glue the fragments into a persona.
If you’re working on an application that has been around for a while, you should (hopefully) have ample data to sift through. If you’re creating a new application, I’ll have instructions and advice for you in a later post.
Before data sifting, ask some basic questions:
- How have my application/service and/or users been attacked?
- Where are the villainous users coming from?
- What are the common traits of those villainous users?
Now sleuth through that data, identifying themes and traits like the use of common phrases in member bios. One actual company was able to catch its villainous users when they wrote, “Kindly, send me a…” or, “I’m a reverend” in their member bios. Strange, but true. Closely related email addresses and passwords for multiple accounts would be another telltale clue. Another example would be insisting on banking information. This is a common goal of “dark” users. Mark it in the persona.
3. Build your personas
Once you’ve identified the common themes and traits of your fraudulent users, build your persona. Here’s an example:
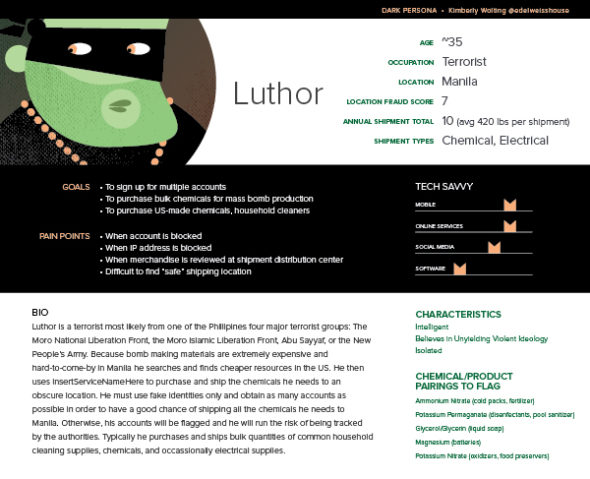
In reviewing the data for our fake persona above, a few common themes emerged that indicated villainous users were primarily from Manila, created multiple accounts that shared the same password, and often ordered chemicals in bulk and in peculiar and repeatable pairings.
4. Build your flow maps
 Using your villainous personas, create a flow map that walks your persona through your experience.
Using your villainous personas, create a flow map that walks your persona through your experience.
The common persona traits and themes you developed will allow you to build flags into your flow map. Every time a villainous user trips one of your flags, your developers can build in features to tag the account. Trip too many flags, and the villainous user is blocked and reported to the right people.
Here is a small piece of the flow map broken out.
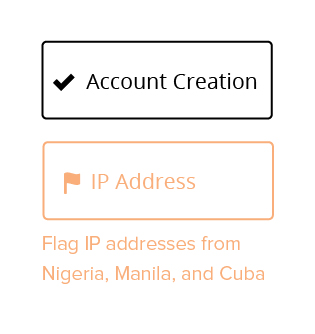
It identifies the step of the process and one of the flagged areas within that step. This is a document you will share and review with your developers. It’s vitally important to make sure they’re aware of each step of this process.
Here is how that piece correlates to a larger system.

What’s interesting to note is that when you build a flow map for a “light” user, you are ensuring that the flow of the system is intuitive and usable. On the other hand, when building for a villainous user, you’re preventing or hindering them from using your app at all.
5. Last step–update!
Villainous personas, arguably even more so than “light” personas, are living documents.
Like I stated before, the fraud industry is constantly shifting and discovering new strategies. In the same way that we update our “light” personas to understand their changing motivations and goals, we need to stay constantly vigilant about our villainous personas. You will build excellent walls, and they will find new ways to knock them down. Be ready.
When you signed up to be a UX designer, you probably didn’t realize that you could also add detective to your resume! If you’re not picking up and embracing the Sherlock vibe I’m throwing your way, you should, but instead of a magnifying glass and deerstalker hat, your investigative tools are personas and flow maps.
The idea is simple: Learn everything you can about the users you don’t want so that you can prevent, block, or report them from engaging in the experience you are building.
If you’ve developed a similar system, let’s talk about it. We are, after all, fighting the good fight together.
Good luck, and may the dark side be with you.

I think you forgot the most common “evildoer” fakes and trolls , I feel like signing up for target bad behavior is a problem, but widespread false information and misusage without a focus may bring down a service to it’s knees