Article summary
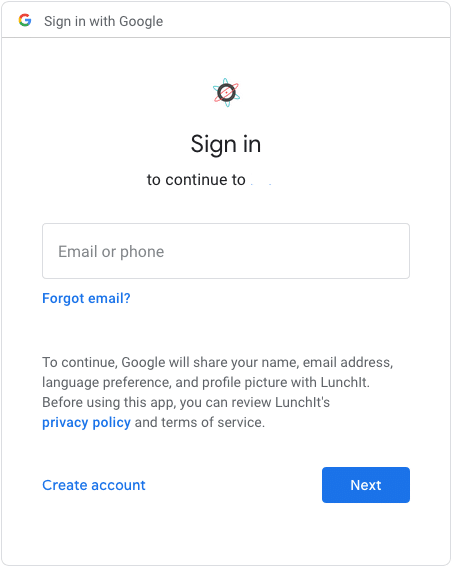 If you’re using Google Chrome or one of Google’s many apps, you’ve probably seen a screen similar to this one.
If you’re using Google Chrome or one of Google’s many apps, you’ve probably seen a screen similar to this one.
You can achieve this for your internal websites or mobile apps using an Apache server and Google’s OpenID Connect 1.0. This is a simple identity layer on top of the OAuth 2.0 protocol (Google’s authentication system for user logins).
Google Configurations
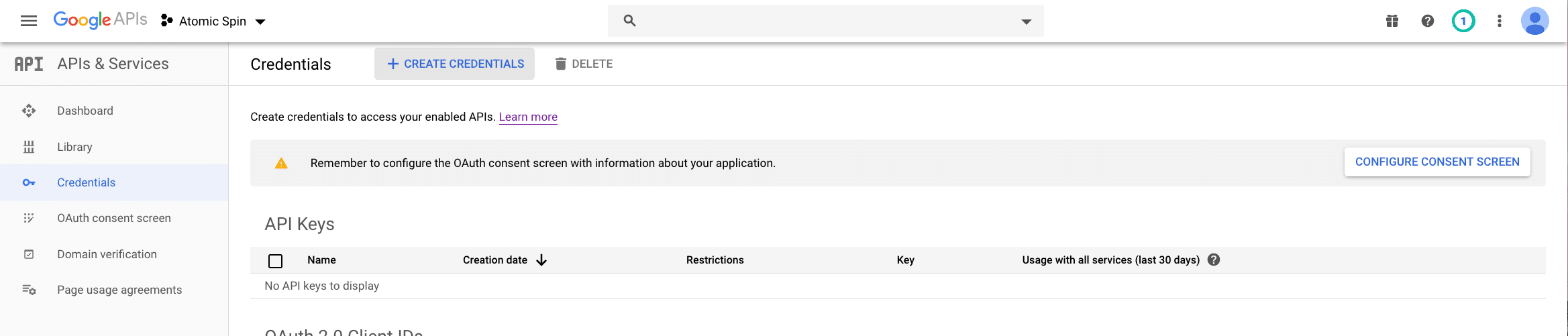
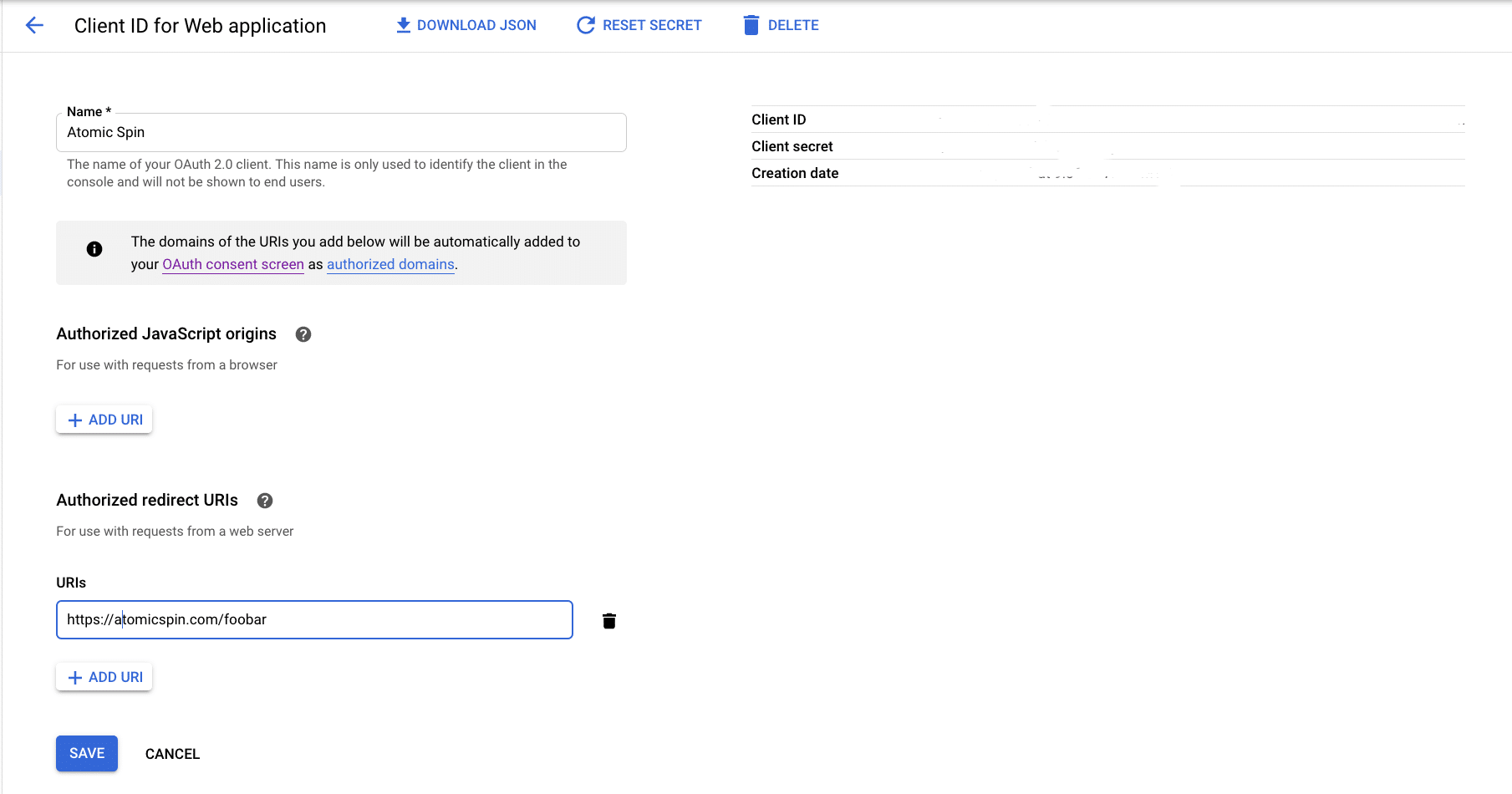
To use this system, you’ll need to do some configuration at the Google API Console. First, obtain OAuth 2.0 credentials and set a redirect on the Credentials page:
Then customize the user consent screen:
Apache Server Setup
To configure your Apache server, you’ll need to edit the virtual host configuration. You will configure that file with mod_auth_openidc. This is an Apache 2.xx HTTP server authentication/authorization module that authenticates users against the OpenID Connect Provider (what we just set up with Google). It’s an Open Connect Relying Party and is OpenID Certified.
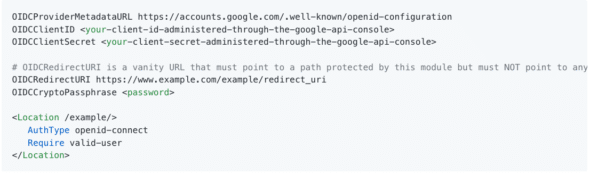
Thankfully, mod_auth_openidc has great instructions on how to configure your virtual host file specifically to work with Google’s Single Sign-On. Get the personalized data from the Google Credentials page and enter it in the placeholders below:
All in all, this is a simple project to protect your apps with Google Single Sign-On. It gives the user one fewer step when they need to be logged in to multiple apps, and it’s a familiar screen that lets them know their data will be secure.